I wanted to setup a TACACS+ server to provide AAA(Authentication, Authorization, Accounting) for my Cisco routers running under GNS3.
Bit of searching found me the "Free TACACS+ Server" software offered here: http://www.tacacs.net/
So I decided that I would set this on a Ubuntu machine running on VMWare. My Ubuntu box was already set up on VMWare as I was using it for other purposes. Before I connected it to GNS3 I wanted to install TACACS+. This is because I am going to connect it with GNS3 using the "(Host Only)" method in VMware and give it a static IP address to talk with the router. In doing this I will loose my internet connection for this Ubuntu box running on VMWare. As I plan to create a clone of this machine and keep it separately as my TACACS+ server for future labs/studies, here's how I did it..
fist I checked this package tacacs+ to make sure what I am going to install:
root@ubuntu:~# aptitude show tacacs+
Package: tacacs+
State: not installed
Version: 4.0.4.19-11build1
Priority: extra
Section: universe/net
Maintainer: Ubuntu Developers <ubuntu-devel-discuss@lists.ubuntu.com>
Architecture: i386
Uncompressed Size: 233 k
Depends: libc6 (>= 2.7), libpam0g (>= 0.99.7.1), libtacacs+1, libwrap0 (>=
7.6-4~), adduser, python
Description: TACACS+ authentication daemon
TACACS+ is a protocol (not TACACS or XTACACS) for authentication, authorization
and accounting (AAA) services for routers and network devices.
Homepage: http://www.shrubbery.net/tac_plus/
Yup, looks good. I went ahead and installed it
root@ubuntu:~# aptitude install tacacs+
Now that I am done installing TACACS+ on this machine I am going to go ahead and clone this as mentioned earlier. You can easily use the tools in VMWare to do this
Okay now I have got my clone which I’d be using from now on as my TACACS+ server. To connect this with GNS3, I need to set up the network interface properly.
I selected the new clone and I can see it’s properties on the left-side panel:
Double click on the “Network Adaptor” show above and you’ll get the screen to customize the network adaptor settings. We need to set “Network Connection” to a “(Host Only)” connection. And that’s what I did:
You can find more information on how to connect your VMWare hosts with GNS3 on this article: http://blog.skufel.net/2011/12/vmware-workstation-8-and-gns3-integration/
Basically when you do the above, VMware will create a virtual network adaptor for you. And that virtual adapter will appear on your adaptors list. Mine appears as “VMware Network Adapter VMNet1” : So now on GNS3 you can simply add a host and configure it to use this Virtual adapter as it’s Ethernet interface:
So now on GNS3 you can simply add a host and configure it to use this Virtual adapter as it’s Ethernet interface: After that your VMware host is connected to GNS3. Make you you set the static IP address and default gateway on your Virtual host so it can talk with the router. I want to set the static IP of 10.3.0.20 with the default gateway of 10.3.0.1.You can do this by editing the "/etc/networking/interface" file on your virtual host. But I had ran into some problems where it seems to neglect the default gateway I specified. So instead I used the GUI to set my static IP address:
After that your VMware host is connected to GNS3. Make you you set the static IP address and default gateway on your Virtual host so it can talk with the router. I want to set the static IP of 10.3.0.20 with the default gateway of 10.3.0.1.You can do this by editing the "/etc/networking/interface" file on your virtual host. But I had ran into some problems where it seems to neglect the default gateway I specified. So instead I used the GUI to set my static IP address: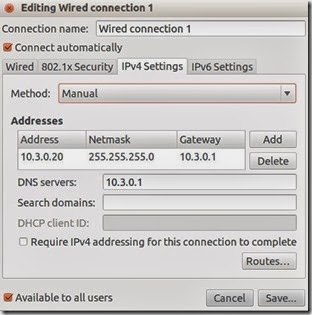 Perfect! We are ready to test connectivity. Here’s my GNS3 topology:
Perfect! We are ready to test connectivity. Here’s my GNS3 topology: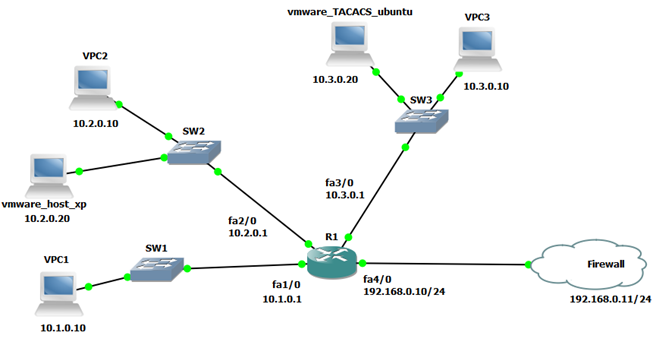 The ‘vmware_TACACS_ubuntu’ host you see at the top is the one we just configured. Great.. now fingers crossed and let’s test connectivity between this host and router R1:
The ‘vmware_TACACS_ubuntu’ host you see at the top is the one we just configured. Great.. now fingers crossed and let’s test connectivity between this host and router R1:root@ubuntu:/etc/network# ping 10.3.0.1Yay! we have connectivity.
PING 10.3.0.1 (10.3.0.1) 56(84) bytes of data.
64 bytes from 10.3.0.1: icmp_req=1 ttl=255 time=14.1 ms
64 bytes from 10.3.0.1: icmp_req=2 ttl=255 time=12.0 ms
64 bytes from 10.3.0.1: icmp_req=3 ttl=255 time=22.1 ms
64 bytes from 10.3.0.1: icmp_req=4 ttl=255 time=22.5 ms
64 bytes from 10.3.0.1: icmp_req=5 ttl=255 time=21.0 ms
sudo gedit tac_plus.confOne of the items we want to set is the secret(password) that the router can use to communicate with this tacacs+ server.
# This is the key that clients have to use to access Tacacs+..And where the accounting file is so that it can record(store) data of what users have been up to:
key = testing123
# Define where to log accounting data, this is the default.As I wanted to make sure the above file was available, I went into the '/var/log' folder and created the blank file with:
accounting file = /var/log/tac_plus.acct
sudo touch tac_plus.acctthen I made sure that anyone can write to it(ok for a test but not a good idea for a production environment!):
sudo chmod a+rw tac_plus.acctAgain inside the ‘tac_plus.conf’ file, I commented out the part where it says use PAM for user authentication and I manually added my test user. Who is "admin" with the password "cisco123". Of Couse this is not a good security measure for a production environment but we are just doing to for a test here.
user = admin {
default service = permit
login = cleartext cisco123
# the following will provide 'admin' user with an exec
# shell(mode) with privilege level '15'. (Activated by
# the 'aaa authorization exec..' command on router)
service = exec {
priv-lvl = 15
}
}Okay.. all the necessary configs seem to be done. Let's go ahead and restart the tacacs+ server for the changes to take affect:root@ubuntu:/etc/tacacs+# /etc/init.d/tacacs_plus restartQuick check confirms that our new TACACS+ server baby is running:
* Restarting TACACS+ authentication daemon tacacs+
root@ubuntu:/etc/tacacs+# netstat -tnlp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 1411/apache2
tcp 0 0 0.0.0.0:49 0.0.0.0:* LISTEN 3194/tac_plus
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 1191/dnsmasq
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1130/cupsd
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN 1320/mysqld
tcp6 0 0 ::1:631 :::* LISTEN 1130/cupsd
Now let's head back to our R1 console in GNS3 to see if the router can actually access our TACACS+ server
R1(config)#tacacs-server ?
administration Start tacacs+ daemon handling administrative messages
directed-request Allow user to specify tacacs server to use with `@server'
dns-alias-lookup Enable IP Domain Name System Alias lookup for TACACS
servers
domain-stripping Strip the domain from the username
host Specify a TACACS server
key Set TACACS+ encryption key.
packet Modify TACACS+ packet options
timeout Time to wait for a TACACS server to reply
We set the TACACS+ server host location with:
R1(config)#tacacs-server host 10.3.0.20And the password key to encrypt communication between routers and server. This is the one we set earlier inside the /etc/tacacs+/tac_plus.conf file
R1(config)#
R1(config)#tacacs-server key testing123
Alrighty.. Now the moment of truth. Let's authenticate a user against our TACAC+ server. Remember we set up a test user with username: admin, password: cisco123 earlier inside the tac_plus.conf file. Let’s test if we can authenticate that user:
R1#test aaa group tacacs+ admin cisco123 legacy
Attempting authentication test to server-group tacacs+ using tacacs+
User was successfully authenticated.
Hooray! we did it. The user "admin" is successfully authenticated. Just for a quick test, if we give the wrong password, it will not work:
R1#test aaa group tacacs+ admin somewrongPass legacy
Attempting authentication test to server-group tacacs+ using tacacs+
User authentication request was rejected by server.
Done.. Now our TACACS+ server is ready for use.
My Resources & References:
- http://www.ipbalance.com/security/tacacs/149-tacacs-plus-installation.html
- http://www.tacacs.net/
- http://blog.skufel.net/2011/12/vmware-workstation-8-and-gns3-integration/
- http://network-chef.blogspot.com.au/2013/04/free-tacacs-server.html
- http://popravak.wordpress.com/2013/08/07/connecting-vmware-workstation-and-cisco-gns3-lab/
- http://www.howtoforge.com/linux-basics-set-a-static-ip-on-ubuntu
- http://www.cyberciti.biz/faq/linux-configure-a-static-ip-address-tutorial/
- http://www.cisco.com/en/US/tech/tk59/technologies_tech_note09186a008009465c.shtml#t6






1 comment :
FYI: While testing I've found that I need to add the following line to allow authorization by default:
#default authentication = file /etc/passwd
default authorization = permit
Post a Comment